Search Results for author: Raghavendra Ramachandra
Found 45 papers, 10 papers with code
NTIRE 2024 Challenge on Image Super-Resolution ($\times$4): Methods and Results
1 code implementation • 15 Apr 2024 • Zheng Chen, Zongwei Wu, Eduard Zamfir, Kai Zhang, Yulun Zhang, Radu Timofte, Xiaokang Yang, Hongyuan Yu, Cheng Wan, Yuxin Hong, Zhijuan Huang, Yajun Zou, Yuan Huang, Jiamin Lin, Bingnan Han, Xianyu Guan, Yongsheng Yu, Daoan Zhang, Xuanwu Yin, Kunlong Zuo, Jinhua Hao, Kai Zhao, Kun Yuan, Ming Sun, Chao Zhou, Hongyu An, Xinfeng Zhang, Zhiyuan Song, Ziyue Dong, Qing Zhao, Xiaogang Xu, Pengxu Wei, Zhi-chao Dou, Gui-ling Wang, Chih-Chung Hsu, Chia-Ming Lee, Yi-Shiuan Chou, Cansu Korkmaz, A. Murat Tekalp, Yubin Wei, Xiaole Yan, Binren Li, Haonan Chen, Siqi Zhang, Sihan Chen, Amogh Joshi, Nikhil Akalwadi, Sampada Malagi, Palani Yashaswini, Chaitra Desai, Ramesh Ashok Tabib, Ujwala Patil, Uma Mudenagudi, Anjali Sarvaiya, Pooja Choksy, Jagrit Joshi, Shubh Kawa, Kishor Upla, Sushrut Patwardhan, Raghavendra Ramachandra, Sadat Hossain, Geongi Park, S. M. Nadim Uddin, Hao Xu, Yanhui Guo, Aman Urumbekov, Xingzhuo Yan, Wei Hao, Minghan Fu, Isaac Orais, Samuel Smith, Ying Liu, Wangwang Jia, Qisheng Xu, Kele Xu, Weijun Yuan, Zhan Li, Wenqin Kuang, Ruijin Guan, Ruting Deng, Zhao Zhang, Bo wang, Suiyi Zhao, Yan Luo, Yanyan Wei, Asif Hussain Khan, Christian Micheloni, Niki Martinel
This paper reviews the NTIRE 2024 challenge on image super-resolution ($\times$4), highlighting the solutions proposed and the outcomes obtained.
FH-SSTNet: Forehead Creases based User Verification using Spatio-Spatial Temporal Network
no code implementations • 24 Mar 2024 • Geetanjali Sharma, Gaurav Jaswal, Aditya Nigam, Raghavendra Ramachandra
The results demonstrate the superior performance of FH-SSTNet for forehead-based user verification, confirming its effectiveness in identity authentication.
Does complimentary information from multispectral imaging improve face presentation attack detection?
no code implementations • 20 Nov 2023 • Narayan Vetrekar, Raghavendra Ramachandra, Sushma Venkatesh, Jyoti D. Pawar, R. S. Gad
We present PAD based on multispectral images constructed for eight different presentation artifacts resulted from three different artifact species.
SynFacePAD 2023: Competition on Face Presentation Attack Detection Based on Privacy-aware Synthetic Training Data
1 code implementation • 9 Nov 2023 • Meiling Fang, Marco Huber, Julian Fierrez, Raghavendra Ramachandra, Naser Damer, Alhasan Alkhaddour, Maksim Kasantcev, Vasiliy Pryadchenko, Ziyuan Yang, Huijie Huangfu, Yingyu Chen, Yi Zhang, Yuchen Pan, Junjun Jiang, Xianming Liu, Xianyun Sun, Caiyong Wang, Xingyu Liu, Zhaohua Chang, Guangzhe Zhao, Juan Tapia, Lazaro Gonzalez-Soler, Carlos Aravena, Daniel Schulz
This paper presents a summary of the Competition on Face Presentation Attack Detection Based on Privacy-aware Synthetic Training Data (SynFacePAD 2023) held at the 2023 International Joint Conference on Biometrics (IJCB 2023).
Fingervein Verification using Convolutional Multi-Head Attention Network
no code implementations • 25 Oct 2023 • Raghavendra Ramachandra, Sushma Venkatesh
The proposed VeinAtnNet was trained on the newly constructed fingervein dataset with 300 unique fingervein patterns that were captured in multiple sessions to obtain 92 samples per unique fingervein.
ExtSwap: Leveraging Extended Latent Mapper for Generating High Quality Face Swapping
1 code implementation • 19 Oct 2023 • Aravinda Reddy PN, K. Sreenivasa Rao, Raghavendra Ramachandra, Pabitra Mitra
We present a novel face swapping method using the progressively growing structure of a pre-trained StyleGAN.
Sound-Print: Generalised Face Presentation Attack Detection using Deep Representation of Sound Echoes
no code implementations • 24 Sep 2023 • Raghavendra Ramachandra, Jag Mohan Singh, Sushma Venkatesh
In this paper, we present an acoustic echo-based face Presentation Attack Detection (PAD) on a smartphone in which the PAs are detected based on the reflection profiles of the transmitted signal.
Deep Features for Contactless Fingerprint Presentation Attack Detection: Can They Be Generalized?
no code implementations • 4 Jul 2023 • Hailin Li, Raghavendra Ramachandra
The rapid evolution of high-end smartphones with advanced high-resolution cameras has resulted in contactless capture of fingerprint biometrics that are more reliable and suitable for verification.
Deep Learning based Fingerprint Presentation Attack Detection: A Comprehensive Survey
no code implementations • 27 May 2023 • Hailin Li, Raghavendra Ramachandra
The vulnerabilities of fingerprint authentication systems have raised security concerns when adapting them to highly secure access-control applications.
Differential Newborn Face Morphing Attack Detection using Wavelet Scatter Network
no code implementations • 2 May 2023 • Raghavendra Ramachandra, Sushma Venkatesh, Guoqiang Li, Kiran Raja
Face Recognition System (FRS) are shown to be vulnerable to morphed images of newborns.
Multispectral Imaging for Differential Face Morphing Attack Detection: A Preliminary Study
no code implementations • 7 Apr 2023 • Raghavendra Ramachandra, Sushma Venkatesh, Naser Damer, Narayan Vetrekar, Rajendra Gad
The D-MAD methods are based on using two facial images that are captured from the ePassport (also called the reference image) and the trusted device (for example, Automatic Border Control (ABC) gates) to detect whether the face image presented in ePassport is morphed.
A Latent Fingerprint in the Wild Database
no code implementations • 3 Apr 2023 • Xinwei Liu, Kiran Raja, Renfang Wang, Hong Qiu, Hucheng Wu, Dechao Sun, Qiguang Zheng, Nian Liu, Xiaoxia Wang, Gehang Huang, Raghavendra Ramachandra, Christoph Busch
Further, existing databases for latent fingerprint recognition do not have a large number of unique subjects/fingerprint instances or do not provide ground truth/reference fingerprint images to conduct a cross-comparison against the latent.
Vulnerability of Face Morphing Attacks: A Case Study on Lookalike and Identical Twins
no code implementations • 24 Mar 2023 • Raghavendra Ramachandra, Sushma Venkatesh, Gaurav Jaswal, Guoqiang Li
We present a systematic study on benchmarking the vulnerability of Face Recognition Systems (FRS) to lookalike and identical twin morphing images.
NewsNet: A Novel Dataset for Hierarchical Temporal Segmentation
no code implementations • CVPR 2023 • Haoqian Wu, Keyu Chen, Haozhe Liu, Mingchen Zhuge, Bing Li, Ruizhi Qiao, Xiujun Shu, Bei Gan, Liangsheng Xu, Bo Ren, Mengmeng Xu, Wentian Zhang, Raghavendra Ramachandra, Chia-Wen Lin, Bernard Ghanem
Temporal video segmentation is the get-to-go automatic video analysis, which decomposes a long-form video into smaller components for the following-up understanding tasks.
Finger-NestNet: Interpretable Fingerphoto Verification on Smartphone using Deep Nested Residual Network
no code implementations • 9 Dec 2022 • Raghavendra Ramachandra, Hailin Li
Fingerphoto images captured using a smartphone are successfully used to verify the individuals that have enabled several applications.
SRTGAN: Triplet Loss based Generative Adversarial Network for Real-World Super-Resolution
no code implementations • 22 Nov 2022 • Dhruv Patel, Abhinav Jain, Simran Bawkar, Manav Khorasiya, Kalpesh Prajapati, Kishor Upla, Kiran Raja, Raghavendra Ramachandra, Christoph Busch
We introduce a new triplet-based adversarial loss function that exploits the information provided in the LR image by using it as a negative sample.
Deep Composite Face Image Attacks: Generation, Vulnerability and Detection
1 code implementation • 20 Nov 2022 • Jag Mohan Singh, Raghavendra Ramachandra
Given the face images corresponding to two unique data subjects, the proposed CFIA method will independently generate the segmented facial attributes, then blend them using transparent masks to generate the CFIA samples.
Reliable Face Morphing Attack Detection in On-The-Fly Border Control Scenario with Variation in Image Resolution and Capture Distance
no code implementations • 30 Sep 2022 • Jag Mohan Singh, Raghavendra Ramachandra
Among these attacks, face morphing attacks are highly potential in deceiving automatic FRS and human observers and indicate a severe security threat, especially in the border control scenario.
A Uniform Representation Learning Method for OCT-based Fingerprint Presentation Attack Detection and Reconstruction
no code implementations • 25 Sep 2022 • Wentian Zhang, Haozhe Liu, Feng Liu, Raghavendra Ramachandra
For reconstruction performance, our method achieves the best performance with 0. 834 mIOU and 0. 937 PA. By comparing with the recognition performance on surface 2D fingerprints, the effectiveness of our proposed method on high quality subsurface fingerprint reconstruction is further proved.
Time flies by: Analyzing the Impact of Face Ageing on the Recognition Performance with Synthetic Data
no code implementations • 17 Aug 2022 • Marcel Grimmer, Haoyu Zhang, Raghavendra Ramachandra, Kiran Raja, Christoph Busch
The vast progress in synthetic image synthesis enables the generation of facial images in high resolution and photorealism.
SYN-MAD 2022: Competition on Face Morphing Attack Detection Based on Privacy-aware Synthetic Training Data
1 code implementation • 15 Aug 2022 • Marco Huber, Fadi Boutros, Anh Thi Luu, Kiran Raja, Raghavendra Ramachandra, Naser Damer, Pedro C. Neto, Tiago Gonçalves, Ana F. Sequeira, Jaime S. Cardoso, João Tremoço, Miguel Lourenço, Sergio Serra, Eduardo Cermeño, Marija Ivanovska, Borut Batagelj, Andrej Kronovšek, Peter Peer, Vitomir Štruc
The competition attracted a total of 12 participating teams, both from academia and industry and present in 11 different countries.
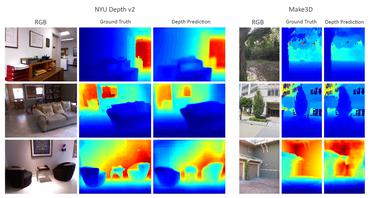
How Far Can I Go ? : A Self-Supervised Approach for Deterministic Video Depth Forecasting
1 code implementation • 1 Jul 2022 • Sauradip Nag, Nisarg Shah, Anran Qi, Raghavendra Ramachandra
Unlike previous methods, we model the depth estimation of the unobserved frame as a view-synthesis problem, which treats the depth estimate of the unseen video frame as an auxiliary task while synthesizing back the views using learned pose.
Analyzing Human Observer Ability in Morphing Attack Detection -- Where Do We Stand?
no code implementations • 24 Feb 2022 • Sankini Rancha Godage, Frøy Løvåsdal, Sushma Venkatesh, Kiran Raja, Raghavendra Ramachandra, Christoph Busch
One prevalent misconception is that an examiner's or observer's capacity for facial morph detection depends on their subject expertise, experience, and familiarity with the issue and that no works have reported the specific results of observers who regularly verify identity (ID) documents for their jobs.
3D Face Morphing Attacks: Generation, Vulnerability and Detection
1 code implementation • 10 Jan 2022 • Jag Mohan Singh, Raghavendra Ramachandra
To this extent, we introduced a novel approach based on blending 3D face point clouds corresponding to contributory data subjects.
Generation of Non-Deterministic Synthetic Face Datasets Guided by Identity Priors
no code implementations • 7 Dec 2021 • Marcel Grimmer, Haoyu Zhang, Raghavendra Ramachandra, Kiran Raja, Christoph Busch
Mated samples are generated by manipulating latent vectors, and more precisely, we exploit Principal Component Analysis (PCA) to define semantically meaningful directions in the latent space and control the similarity between the original and the mated samples using a pre-trained face recognition system.
Algorithmic Fairness in Face Morphing Attack Detection
no code implementations • 23 Nov 2021 • Raghavendra Ramachandra, Kiran Raja, Christoph Busch
In this paper, we study and present a comprehensive analysis of algorithmic fairness of the existing Single image-based Morph Attack Detection (S-MAD) algorithms.
FRT-PAD: Effective Presentation Attack Detection Driven by Face Related Task
1 code implementation • 22 Nov 2021 • Wentian Zhang, Haozhe Liu, Feng Liu, Raghavendra Ramachandra, Christoph Busch
The proposed method, first introduces task specific features from other face related task, then, we design a Cross-Modal Adapter using a Graph Attention Network (GAT) to re-map such features to adapt to PAD task.
DFCANet: Dense Feature Calibration-Attention Guided Network for Cross Domain Iris Presentation Attack Detection
no code implementations • 1 Nov 2021 • Gaurav Jaswal, Aman Verma, Sumantra Dutta Roy, Raghavendra Ramachandra
To alleviate these shortcomings, this paper proposes DFCANet: Dense Feature Calibration and Attention Guided Network which calibrates the locally spread iris patterns with the globally located ones.
 Cross-Domain Iris Presentation Attack Detection
Cross-Domain Iris Presentation Attack Detection
 Incremental Learning
+1
Incremental Learning
+1
Multilingual Audio-Visual Smartphone Dataset And Evaluation
no code implementations • 9 Sep 2021 • Hareesh Mandalapu, Aravinda Reddy P N, Raghavendra Ramachandra, K Sreenivasa Rao, Pabitra Mitra, S R Mahadeva Prasanna, Christoph Busch
This new dataset contains 103 subjects captured in three different sessions considering the different real-world scenarios.
Taming Self-Supervised Learning for Presentation Attack Detection: De-Folding and De-Mixing
1 code implementation • 9 Sep 2021 • Zhe Kong, Wentian Zhang, Feng Liu, Wenhan Luo, Haozhe Liu, Linlin Shen, Raghavendra Ramachandra
Even though there are numerous Presentation Attack Detection (PAD) techniques based on both deep learning and hand-crafted features, the generalization of PAD for unknown PAI is still a challenging problem.
ReGenMorph: Visibly Realistic GAN Generated Face Morphing Attacks by Attack Re-generation
no code implementations • 20 Aug 2021 • Naser Damer, Kiran Raja, Marius Süßmilch, Sushma Venkatesh, Fadi Boutros, Meiling Fang, Florian Kirchbuchner, Raghavendra Ramachandra, Arjan Kuijper
Face morphing attacks aim at creating face images that are verifiable to be the face of multiple identities, which can lead to building faulty identity links in operations like border checks.
MFR 2021: Masked Face Recognition Competition
no code implementations • 29 Jun 2021 • Fadi Boutros, Naser Damer, Jan Niklas Kolf, Kiran Raja, Florian Kirchbuchner, Raghavendra Ramachandra, Arjan Kuijper, Pengcheng Fang, Chao Zhang, Fei Wang, David Montero, Naiara Aginako, Basilio Sierra, Marcos Nieto, Mustafa Ekrem Erakin, Ugur Demir, Hazim Kemal, Ekenel, Asaki Kataoka, Kohei Ichikawa, Shizuma Kubo, Jie Zhang, Mingjie He, Dan Han, Shiguang Shan, Klemen Grm, Vitomir Štruc, Sachith Seneviratne, Nuran Kasthuriarachchi, Sanka Rasnayaka, Pedro C. Neto, Ana F. Sequeira, Joao Ribeiro Pinto, Mohsen Saffari, Jaime S. Cardoso
These teams successfully submitted 18 valid solutions.
Learned Smartphone ISP on Mobile NPUs with Deep Learning, Mobile AI 2021 Challenge: Report
2 code implementations • 17 May 2021 • Andrey Ignatov, Cheng-Ming Chiang, Hsien-Kai Kuo, Anastasia Sycheva, Radu Timofte, Min-Hung Chen, Man-Yu Lee, Yu-Syuan Xu, Yu Tseng, Shusong Xu, Jin Guo, Chao-Hung Chen, Ming-Chun Hsyu, Wen-Chia Tsai, Chao-Wei Chen, Grigory Malivenko, Minsu Kwon, Myungje Lee, Jaeyoon Yoo, Changbeom Kang, Shinjo Wang, Zheng Shaolong, Hao Dejun, Xie Fen, Feng Zhuang, Yipeng Ma, Jingyang Peng, Tao Wang, Fenglong Song, Chih-Chung Hsu, Kwan-Lin Chen, Mei-Hsuang Wu, Vishal Chudasama, Kalpesh Prajapati, Heena Patel, Anjali Sarvaiya, Kishor Upla, Kiran Raja, Raghavendra Ramachandra, Christoph Busch, Etienne de Stoutz
As the quality of mobile cameras starts to play a crucial role in modern smartphones, more and more attention is now being paid to ISP algorithms used to improve various perceptual aspects of mobile photos.
On the Applicability of Synthetic Data for Face Recognition
no code implementations • 6 Apr 2021 • Haoyu Zhang, Marcel Grimmer, Raghavendra Ramachandra, Kiran Raja, Christoph Busch
Face verification has come into increasing focus in various applications including the European Entry/Exit System, which integrates face recognition mechanisms.
Face Morphing Attack Generation & Detection: A Comprehensive Survey
no code implementations • 3 Nov 2020 • Sushma Venkatesh, Raghavendra Ramachandra, Kiran Raja, Christoph Busch
The vulnerability of Face Recognition System (FRS) to various kind of attacks (both direct and in-direct attacks) and face morphing attacks has received a great interest from the biometric community.
On Benchmarking Iris Recognition within a Head-mounted Display for AR/VR Application
no code implementations • 20 Oct 2020 • Fadi Boutros, Naser Damer, Kiran Raja, Raghavendra Ramachandra, Florian Kirchbuchner, Arjan Kuijper
Motivated by the performance of iris recognition, we also propose the continuous authentication of users in a non-collaborative capture setting in HMD.
MIPGAN -- Generating Strong and High Quality Morphing Attacks Using Identity Prior Driven GAN
no code implementations • 3 Sep 2020 • Haoyu Zhang, Sushma Venkatesh, Raghavendra Ramachandra, Kiran Raja, Naser Damer, Christoph Busch
Extensive experiments are carried out to assess the FRS's vulnerability against the proposed morphed face generation technique on three types of data such as digital images, re-digitized (printed and scanned) images, and compressed images after re-digitization from newly generated MIPGAN Face Morph Dataset.
Adversarial Attacks against Face Recognition: A Comprehensive Study
no code implementations • 22 Jul 2020 • Fatemeh Vakhshiteh, Ahmad Nickabadi, Raghavendra Ramachandra
Face recognition (FR) systems have demonstrated outstanding verification performance, suggesting suitability for real-world applications ranging from photo tagging in social media to automated border control (ABC).
Can GAN Generated Morphs Threaten Face Recognition Systems Equally as Landmark Based Morphs? -- Vulnerability and Detection
no code implementations • 7 Jul 2020 • Sushma Venkatesh, Haoyu Zhang, Raghavendra Ramachandra, Kiran Raja, Naser Damer, Christoph Busch
\textit{(i) Can GAN generated morphs threaten Face Recognition Systems (FRS) equally as Landmark based morphs?}
On the Influence of Ageing on Face Morph Attacks: Vulnerability and Detection
no code implementations • 6 Jul 2020 • Sushma Venkatesh, Kiran Raja, Raghavendra Ramachandra, Christoph Busch
To this extent, we have introduced a new morphed face dataset with ageing derived from the publicly available MORPH II face dataset, which we refer to as MorphAge dataset.
Morphing Attack Detection -- Database, Evaluation Platform and Benchmarking
no code implementations • 11 Jun 2020 • Kiran Raja, Matteo Ferrara, Annalisa Franco, Luuk Spreeuwers, Illias Batskos, Florens de Wit Marta Gomez-Barrero, Ulrich Scherhag, Daniel Fischer, Sushma Venkatesh, Jag Mohan Singh, Guoqiang Li, Loïc Bergeron, Sergey Isadskiy, Raghavendra Ramachandra, Christian Rathgeb, Dinusha Frings, Uwe Seidel, Fons Knopjes, Raymond Veldhuis, Davide Maltoni, Christoph Busch
Further, we present a new online evaluation platform to test algorithms on sequestered data.
A Survey on Unknown Presentation Attack Detection for Fingerprint
no code implementations • 17 May 2020 • Jag Mohan Singh, Ahmed Madhun, Guoqiang Li, Raghavendra Ramachandra
Fingerprint recognition systems are widely deployed in various real-life applications as they have achieved high accuracy.
Smartphone Multi-modal Biometric Authentication: Database and Evaluation
no code implementations • 5 Dec 2019 • Raghavendra Ramachandra, Martin Stokkenes, Amir Mohammadi, Sushma Venkatesh, Kiran Raja, Pankaj Wasnik, Eric Poiret, Sébastien Marcel, Christoph Busch
One of the unique features of this dataset is that it is collected in four different geographic locations representing a diverse population and ethnicity.
Detecting Finger-Vein Presentation Attacks Using 3D Shape & Diffuse Reflectance Decomposition
no code implementations • 3 Dec 2019 • Jag Mohan Singh, Sushma Venkatesh, Kiran B. Raja, Raghavendra Ramachandra, Christoph Busch
We establish the superiority of the proposed approach by benchmarking it with classical textural feature-descriptor applied directly on finger-vein images.
Robust Morph-Detection at Automated Border Control Gate using Deep Decomposed 3D Shape and Diffuse Reflectance
no code implementations • 3 Dec 2019 • Jag Mohan Singh, Raghavendra Ramachandra, Kiran B. Raja, Christoph Busch
Face recognition is widely employed in Automated Border Control (ABC) gates, which verify the face image on passport or electronic Machine Readable Travel Document (eMTRD) against the captured image to confirm the identity of the passport holder.