Search Results for author: Xinpeng Zhang
Found 51 papers, 9 papers with code
Regeneration Based Training-free Attribution of Fake Images Generated by Text-to-Image Generative Models
no code implementations • 3 Mar 2024 • Meiling Li, Zhenxing Qian, Xinpeng Zhang
Comprehensive experiments reveal that (1) Our method can effectively attribute fake images to their source models, achieving comparable attribution performance with the state-of-the-art method; (2) Our method has high scalability ability, which is well adapted to real-world attribution scenarios.
Purified and Unified Steganographic Network
1 code implementation • 27 Feb 2024 • Guobiao Li, Sheng Li, Zicong Luo, Zhenxing Qian, Xinpeng Zhang
It is also shown to be capable of imperceptibly carrying the steganographic networks in a purified network.
Object-oriented backdoor attack against image captioning
no code implementations • 5 Jan 2024 • Meiling Li, Nan Zhong, Xinpeng Zhang, Zhenxing Qian, Sheng Li
After training with the poisoned data, the attacked model behaves normally on benign images, but for poisoned images, the model will generate some sentences irrelevant to the given image.
PROMPT-IML: Image Manipulation Localization with Pre-trained Foundation Models Through Prompt Tuning
no code implementations • 1 Jan 2024 • Xuntao Liu, Yuzhou Yang, Qichao Ying, Zhenxing Qian, Xinpeng Zhang, Sheng Li
We observe that humans tend to discern the authenticity of an image based on both semantic and high-frequency information, inspired by which, the proposed framework leverages rich semantic knowledge from pre-trained visual foundation models to assist IML.
From Covert Hiding to Visual Editing: Robust Generative Video Steganography
no code implementations • 1 Jan 2024 • Xueying Mao, Xiaoxiao Hu, Wanli Peng, Zhenliang Gan, Qichao Ying, Zhenxing Qian, Sheng Li, Xinpeng Zhang
Traditional video steganography methods are based on modifying the covert space for embedding, whereas we propose an innovative approach that embeds secret message within semantic feature for steganography during the video editing process.
Model Copyright Protection in Buyer-seller Environment
no code implementations • 5 Dec 2023 • Yusheng Guo, Nan Zhong, Zhenxing Qian, Xinpeng Zhang
The main idea of ISNN is to make a DNN sensitive to the key and copyright information.
Steal My Artworks for Fine-tuning? A Watermarking Framework for Detecting Art Theft Mimicry in Text-to-Image Models
no code implementations • 22 Nov 2023 • Ge Luo, Junqiang Huang, Manman Zhang, Zhenxing Qian, Sheng Li, Xinpeng Zhang
In various fine-tune scenarios and against watermark attack methods, our research confirms that analyzing the distribution of watermarks in artificially generated images reliably detects unauthorized mimicry.
PatchCraft: Exploring Texture Patch for Efficient AI-generated Image Detection
1 code implementation • 21 Nov 2023 • Nan Zhong, Yiran Xu, Sheng Li, Zhenxing Qian, Xinpeng Zhang
We observe that the texture patches of images tend to reveal more traces left by generative models compared to the global semantic information of the images.
Securing Fixed Neural Network Steganography
no code implementations • 18 Sep 2023 • Zicong Luo, Sheng Li, Guobiao Li, Zhenxing Qian, Xinpeng Zhang
To deal with this issue, we propose a key-based FNNS scheme to improve the security of the FNNS, where we generate key-controlled perturbations from the FNN for data embedding.
Salient Object Detection in Optical Remote Sensing Images Driven by Transformer
1 code implementation • 15 Sep 2023 • Gongyang Li, Zhen Bai, Zhi Liu, Xinpeng Zhang, Haibin Ling
KTM models the contextual correlation knowledge of two middle-level features of different scales based on the self-attention mechanism, and transfers the knowledge to the raw features to generate more discriminative features.
Physical Invisible Backdoor Based on Camera Imaging
no code implementations • 14 Sep 2023 • Yusheng Guo, Nan Zhong, Zhenxing Qian, Xinpeng Zhang
Subsequently, we elaborate a special network architecture, which is easily compromised by our backdoor attack, by leveraging the attributes of the CFA interpolation algorithm and combining it with the feature extraction block in the camera identification model.
DRAW: Defending Camera-shooted RAW against Image Manipulation
no code implementations • ICCV 2023 • Xiaoxiao Hu, Qichao Ying, Zhenxing Qian, Sheng Li, Xinpeng Zhang
RAW files are the initial measurement of scene radiance widely used in most cameras, and the ubiquitously-used RGB images are converted from RAW data through Image Signal Processing (ISP) pipelines.
RetouchingFFHQ: A Large-scale Dataset for Fine-grained Face Retouching Detection
no code implementations • 20 Jul 2023 • Qichao Ying, Jiaxin Liu, Sheng Li, Haisheng Xu, Zhenxing Qian, Xinpeng Zhang
However, the lack of large-scale and fine-grained face retouching datasets has been a major obstacle to progress in this field.
Towards Deep Network Steganography: From Networks to Networks
no code implementations • 7 Jul 2023 • Guobiao Li, Sheng Li, Meiling Li, Zhenxing Qian, Xinpeng Zhang
In this paper, we propose deep network steganography for the covert communication of DNN models.
StyleStegan: Leak-free Style Transfer Based on Feature Steganography
no code implementations • 1 Jul 2023 • Xiujian Liang, Bingshan Liu, Qichao Ying, Zhenxing Qian, Xinpeng Zhang
Our method consists of two main components: a style transfer method that accomplishes artistic stylization on the original image and an image steganography method that embeds content feature secrets on the stylized image.
Decision-based iterative fragile watermarking for model integrity verification
no code implementations • 13 May 2023 • Zhaoxia Yin, Heng Yin, Hang Su, Xinpeng Zhang, Zhenzhe Gao
Our method has some advantages: (1) the iterative update of samples is done in a decision-based black-box manner, relying solely on the predicted probability distribution of the target model, which reduces the risk of exposure to adversarial attacks, (2) the small-amplitude multiple iterations approach allows the fragile samples to perform well visually, with a PSNR of 55 dB in TinyImageNet compared to the original samples, (3) even with changes in the overall parameters of the model of magnitude 1e-4, the fragile samples can detect such changes, and (4) the method is independent of the specific model structure and dataset.
Generative Steganographic Flow
no code implementations • 10 May 2023 • Ping Wei, Ge Luo, Qi Song, Xinpeng Zhang, Zhenxing Qian, Sheng Li
In the forward mapping, secret data is hidden in the input latent of Glow model to generate stego images.
Generative Steganography Diffusion
no code implementations • 5 May 2023 • Ping Wei, Qing Zhou, Zichi Wang, Zhenxing Qian, Xinpeng Zhang, Sheng Li
However, existing GAN-based GS methods cannot completely recover the hidden secret data due to the lack of network invertibility, while Flow-based methods produce poor image quality due to the stringent reversibility restriction in each module.
Multi-modal Fake News Detection on Social Media via Multi-grained Information Fusion
no code implementations • 3 Apr 2023 • Yangming Zhou, Yuzhou Yang, Qichao Ying, Zhenxing Qian, Xinpeng Zhang
The easy sharing of multimedia content on social media has caused a rapid dissemination of fake news, which threatens society's stability and security.
Steganography of Steganographic Networks
1 code implementation • 28 Feb 2023 • Guobiao Li, Sheng Li, Meiling Li, Xinpeng Zhang, Zhenxing Qian
We propose to disguise a steganographic network (termed as the secret DNN model) into a stego DNN model which performs an ordinary machine learning task (termed as the stego task).
Lightweight Salient Object Detection in Optical Remote-Sensing Images via Semantic Matching and Edge Alignment
1 code implementation • 7 Jan 2023 • Gongyang Li, Zhi Liu, Xinpeng Zhang, Weisi Lin
Then, semantic kernels are used to activate salient object locations in two groups of high-level features through dynamic convolution operations in DSMM.
Exploring Depth Information for Face Manipulation Detection
no code implementations • 29 Dec 2022 • Haoyue Wang, Meiling Li, Sheng Li, Zhenxing Qian, Xinpeng Zhang
As one of the important face features, the face depth map, which has shown to be effective in other areas such as the face recognition or face detection, is unfortunately paid little attention to in literature for detecting the manipulated face images.
Learning to Immunize Images for Tamper Localization and Self-Recovery
no code implementations • 28 Oct 2022 • Qichao Ying, Hang Zhou, Zhenxing Qian, Sheng Li, Xinpeng Zhang
Image immunization (Imuge) is a technology of protecting the images by introducing trivial perturbation, so that the protected images are immune to the viruses in that the tampered contents can be auto-recovered.
RGB-T Semantic Segmentation with Location, Activation, and Sharpening
1 code implementation • 26 Oct 2022 • Gongyang Li, Yike Wang, Zhi Liu, Xinpeng Zhang, Dan Zeng
The highlight of LASNet is that we fully consider the characteristics of cross-modal features at different levels, and accordingly propose three specific modules for better segmentation.
 Ranked #26 on
Thermal Image Segmentation
on MFN Dataset
Ranked #26 on
Thermal Image Segmentation
on MFN Dataset
Hiding Images in Deep Probabilistic Models
no code implementations • 5 Oct 2022 • Haoyu Chen, Linqi Song, Zhenxing Qian, Xinpeng Zhang, Kede Ma
As an instantiation, we adopt a SinGAN, a pyramid of generative adversarial networks (GANs), to learn the patch distribution of one cover image.
Generative Model Watermarking Based on Human Visual System
no code implementations • 30 Sep 2022 • Li Zhang, Yong liu, Shaoteng Liu, Tianshu Yang, Yexin Wang, Xinpeng Zhang, Hanzhou Wu
Intellectual property protection of deep neural networks is receiving attention from more and more researchers, and the latest research applies model watermarking to generative models for image processing.
Neural network fragile watermarking with no model performance degradation
no code implementations • 16 Aug 2022 • Zhaoxia Yin, Heng Yin, Xinpeng Zhang
In the process of watermarking, we train a generative model with the specific loss function and secret key to generate triggers that are sensitive to the fine-tuning of the target classifier.
Generative Steganography Network
no code implementations • 28 Jul 2022 • Ping Wei, Sheng Li, Xinpeng Zhang, Ge Luo, Zhenxing Qian, Qing Zhou
A new steganographic approach called generative steganography (GS) has emerged recently, in which stego images (images containing secret data) are generated from secret data directly without cover media.
Image Generation Network for Covert Transmission in Online Social Network
no code implementations • 21 Jul 2022 • Zhengxin You, Qichao Ying, Sheng Li, Zhenxing Qian, Xinpeng Zhang
Online social networks have stimulated communications over the Internet more than ever, making it possible for secret message transmission over such noisy channels.
Robust Watermarking for Video Forgery Detection with Improved Imperceptibility and Robustness
no code implementations • 7 Jul 2022 • Yangming Zhou, Qichao Ying, Xiangyu Zhang, Zhenxing Qian, Sheng Li, Xinpeng Zhang
We jointly train a 3D-UNet-based watermark embedding network and a decoder that predicts the tampering mask.
PCPT and ACPT: Copyright Protection and Traceability Scheme for DNN Models
no code implementations • 6 Jun 2022 • Xuefeng Fan, Dahao Fu, Hangyu Gui, Xinpeng Zhang, Xiaoyi Zhou
Because the existing traceability mechanisms are used for models without watermarks, a small number of false-positives are generated.
Image Protection for Robust Cropping Localization and Recovery
no code implementations • 6 Jun 2022 • Qichao Ying, Hang Zhou, Xiaoxiao Hu, Zhenxing Qian, Sheng Li, Xinpeng Zhang
Existing image cropping detection schemes ignore that recovering the cropped-out contents can unveil the purpose of the behaved cropping attack.
A DTCWT-SVD Based Video Watermarking resistant to frame rate conversion
no code implementations • 2 Jun 2022 • Yifei Wang, Qichao Ying, Zhenxing Qian, Sheng Li, Xinpeng Zhang
To address this issue, we present a new video watermarking based on joint Dual-Tree Cosine Wavelet Transformation (DTCWT) and Singular Value Decomposition (SVD), which is resistant to frame rate conversion.
Multimodal Fake News Detection via CLIP-Guided Learning
no code implementations • 28 May 2022 • Yangming Zhou, Qichao Ying, Zhenxing Qian, Sheng Li, Xinpeng Zhang
The results indicate that the proposed framework has a better capability in mining crucial features for fake news detection.
Deniable Steganography
no code implementations • 25 May 2022 • Yong Xu, Zhihua Xia, Zichi Wang, Xinpeng Zhang, Jian Weng
With a stego media discovered, the adversary could find out the sender or receiver and coerce them to disclose the secret message, which we name as coercive attack in this paper.
Imperceptible Backdoor Attack: From Input Space to Feature Representation
1 code implementation • 6 May 2022 • Nan Zhong, Zhenxing Qian, Xinpeng Zhang
A U-net-based network is employed to generate concrete parameters of multinomial distribution for each benign input.
Semantic-Preserving Linguistic Steganography by Pivot Translation and Semantic-Aware Bins Coding
no code implementations • 8 Mar 2022 • Tianyu Yang, Hanzhou Wu, Biao Yi, Guorui Feng, Xinpeng Zhang
In this paper, we propose a novel LS method to modify a given text by pivoting it between two different languages and embed secret data by applying a GLS-like information encoding strategy.
Invertible Image Dataset Protection
no code implementations • 29 Dec 2021 • Kejiang Chen, Xianhan Zeng, Qichao Ying, Sheng Li, Zhenxing Qian, Xinpeng Zhang
We develop a reversible adversarial example generator (RAEG) that introduces slight changes to the images to fool traditional classification models.
From Image to Imuge: Immunized Image Generation
1 code implementation • 27 Oct 2021 • Qichao Ying, Zhenxing Qian, Hang Zhou, Haisheng Xu, Xinpeng Zhang, Siyi Li
At the recipient's side, the verifying network localizes the malicious modifications, and the original content can be approximately recovered by the decoder, despite the presence of the attacks.
Generating Watermarked Adversarial Texts
no code implementations • 25 Oct 2021 • Mingjie Li, Hanzhou Wu, Xinpeng Zhang
Adversarial example generation has been a hot spot in recent years because it can cause deep neural networks (DNNs) to misclassify the generated adversarial examples, which reveals the vulnerability of DNNs, motivating us to find good solutions to improve the robustness of DNN models.
On Generating Identifiable Virtual Faces
no code implementations • 15 Oct 2021 • Zhuowen Yuan, Zhengxin You, Sheng Li, Xinpeng Zhang, Zhenxin Qian, Alex Kot
Our virtual face images are visually different from the original ones for privacy protection.
RWN: Robust Watermarking Network for Image Cropping Localization
no code implementations • 12 Oct 2021 • Qichao Ying, Xiaoxiao Hu, Xiangyu Zhang, Zhenxing Qian, Xinpeng Zhang
At the recipient's side, ACP extracts the watermark from the attacked image, and we conduct feature matching on the original and extracted watermark to locate the position of the crop in the original image plane.
Hiding Images into Images with Real-world Robustness
no code implementations • 12 Oct 2021 • Qichao Ying, Hang Zhou, Xianhan Zeng, Haisheng Xu, Zhenxing Qian, Xinpeng Zhang
The existing image embedding networks are basically vulnerable to malicious attacks such as JPEG compression and noise adding, not applicable for real-world copyright protection tasks.
Exploiting Language Model for Efficient Linguistic Steganalysis
no code implementations • 26 Jul 2021 • Biao Yi, Hanzhou Wu, Guorui Feng, Xinpeng Zhang
Such kind of difference can be naturally captured by the language model used for generating stego texts.
Orientation Convolutional Networks for Image Recognition
no code implementations • 2 Feb 2021 • Yalan Qin, Guorui Feng, Hanzhou Wu, Yanli Ren, Xinpeng Zhang
With the propogation of the low-rank structure, the corresponding sparsity for representation of original Gabor filter bank can be significantly promoted.
Perceptual Robust Hashing for Color Images with Canonical Correlation Analysis
no code implementations • 8 Dec 2020 • Xinran Li, Chuan Qin, Zhenxing Qian, Heng Yao, Xinpeng Zhang
Local color features of significant corner points on outer boundaries of ring-ribbons are extracted through color vector angles (CVA), and color low-order moments (CLMs) is utilized to extract global color features.
Watermarking Graph Neural Networks by Random Graphs
no code implementations • 1 Nov 2020 • Xiangyu Zhao, Hanzhou Wu, Xinpeng Zhang
Many learning tasks require us to deal with graph data which contains rich relational information among elements, leading increasing graph neural network (GNN) models to be deployed in industrial products for improving the quality of service.
Statistical Analysis of Signal-Dependent Noise: Application in Blind Localization of Image Splicing Forgery
no code implementations • 30 Oct 2020 • Mian Zou, Heng Yao, Chuan Qin, Xinpeng Zhang
Through statistical analysis of the SDN model, we assume that noise can be modeled as a Gaussian approximation for a certain brightness and propose a likelihood model for a noise level function.
Invisible Backdoor Attacks on Deep Neural Networks via Steganography and Regularization
1 code implementation • 6 Sep 2019 • Shaofeng Li, Minhui Xue, Benjamin Zi Hao Zhao, Haojin Zhu, Xinpeng Zhang
We show that the proposed invisible backdoors can be fairly effective across various DNN models as well as four datasets MNIST, CIFAR-10, CIFAR-100, and GTSRB, by measuring their attack success rates for the adversary, functionality for the normal users, and invisibility scores for the administrators.
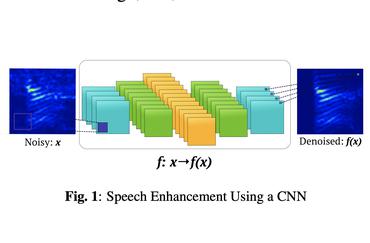
End-to-End Model for Speech Enhancement by Consistent Spectrogram Masking
no code implementations • 2 Jan 2019 • Xingjian Du, Mengyao Zhu, Xuan Shi, Xinpeng Zhang, Wen Zhang, Jingdong Chen
The experiments comparing ourCSM based end-to-end model with other methods are conductedto confirm that the CSM accelerate the model training andhave significant improvements in speech quality.
Robust Degraded Face Recognition Using Enhanced Local Frequency Descriptor and Multi-scale Competition
no code implementations • 3 Oct 2012 • Guangling Sun, Guoqing Li, Xinpeng Zhang
Recognizing degraded faces from low resolution and blurred images are common yet challenging task.