Search Results for author: Weiming Zhang
Found 70 papers, 34 papers with code
DeepFaceLab: Integrated, flexible and extensible face-swapping framework
22 code implementations • 12 May 2020 • Ivan Perov, Daiheng Gao, Nikolay Chervoniy, Kunlin Liu, Sugasa Marangonda, Chris Umé, Mr. Dpfks, Carl Shift Facenheim, Luis RP, Jian Jiang, Sheng Zhang, Pingyu Wu, Bo Zhou, Weiming Zhang
Deepfake defense not only requires the research of detection but also requires the efforts of generation methods.
 Ranked #1 on
Face Swapping
on FaceForensics++
Ranked #1 on
Face Swapping
on FaceForensics++
Ambiguity-Resistant Semi-Supervised Learning for Dense Object Detection
1 code implementation • CVPR 2023 • Chang Liu, Weiming Zhang, Xiangru Lin, Wei zhang, Xiao Tan, Junyu Han, Xiaomao Li, Errui Ding, Jingdong Wang
It employs a "divide-and-conquer" strategy and separately exploits positives for the classification and localization task, which is more robust to the assignment ambiguity.
 Ranked #1 on
Semi-Supervised Object Detection
on COCO 10% labeled data
(detector metric)
Ranked #1 on
Semi-Supervised Object Detection
on COCO 10% labeled data
(detector metric)
CSWin Transformer: A General Vision Transformer Backbone with Cross-Shaped Windows
6 code implementations • CVPR 2022 • Xiaoyi Dong, Jianmin Bao, Dongdong Chen, Weiming Zhang, Nenghai Yu, Lu Yuan, Dong Chen, Baining Guo
By further pretraining on the larger dataset ImageNet-21K, we achieve 87. 5% Top-1 accuracy on ImageNet-1K and high segmentation performance on ADE20K with 55. 7 mIoU.
 Ranked #25 on
Semantic Segmentation
on ADE20K val
Ranked #25 on
Semantic Segmentation
on ADE20K val
HairCLIP: Design Your Hair by Text and Reference Image
1 code implementation • CVPR 2022 • Tianyi Wei, Dongdong Chen, Wenbo Zhou, Jing Liao, Zhentao Tan, Lu Yuan, Weiming Zhang, Nenghai Yu
Hair editing is an interesting and challenging problem in computer vision and graphics.
Multi-attentional Deepfake Detection
1 code implementation • CVPR 2021 • Hanqing Zhao, Wenbo Zhou, Dongdong Chen, Tianyi Wei, Weiming Zhang, Nenghai Yu
Most of them model deepfake detection as a vanilla binary classification problem, i. e, first use a backbone network to extract a global feature and then feed it into a binary classifier (real/fake).
CLIP Itself is a Strong Fine-tuner: Achieving 85.7% and 88.0% Top-1 Accuracy with ViT-B and ViT-L on ImageNet
1 code implementation • 12 Dec 2022 • Xiaoyi Dong, Jianmin Bao, Ting Zhang, Dongdong Chen, Shuyang Gu, Weiming Zhang, Lu Yuan, Dong Chen, Fang Wen, Nenghai Yu
Recent studies have shown that CLIP has achieved remarkable success in performing zero-shot inference while its fine-tuning performance is not satisfactory.
OPERA: Alleviating Hallucination in Multi-Modal Large Language Models via Over-Trust Penalty and Retrospection-Allocation
1 code implementation • 29 Nov 2023 • Qidong Huang, Xiaoyi Dong, Pan Zhang, Bin Wang, Conghui He, Jiaqi Wang, Dahua Lin, Weiming Zhang, Nenghai Yu
Based on the observation, OPERA introduces a penalty term on the model logits during the beam-search decoding to mitigate the over-trust issue, along with a rollback strategy that retrospects the presence of summary tokens in the previously generated tokens, and re-allocate the token selection if necessary.
PeCo: Perceptual Codebook for BERT Pre-training of Vision Transformers
1 code implementation • 24 Nov 2021 • Xiaoyi Dong, Jianmin Bao, Ting Zhang, Dongdong Chen, Weiming Zhang, Lu Yuan, Dong Chen, Fang Wen, Nenghai Yu
This paper explores a better prediction target for BERT pre-training of vision transformers.
E2Style: Improve the Efficiency and Effectiveness of StyleGAN Inversion
2 code implementations • 15 Apr 2021 • Tianyi Wei, Dongdong Chen, Wenbo Zhou, Jing Liao, Weiming Zhang, Lu Yuan, Gang Hua, Nenghai Yu
This paper studies the problem of StyleGAN inversion, which plays an essential role in enabling the pretrained StyleGAN to be used for real image editing tasks.
HairCLIPv2: Unifying Hair Editing via Proxy Feature Blending
1 code implementation • ICCV 2023 • Tianyi Wei, Dongdong Chen, Wenbo Zhou, Jing Liao, Weiming Zhang, Gang Hua, Nenghai Yu
Even though they can enable very fine-grained local control, such interaction modes are inefficient for the editing conditions that can be easily specified by language descriptions or reference images.
Bootstrapped Masked Autoencoders for Vision BERT Pretraining
1 code implementation • 14 Jul 2022 • Xiaoyi Dong, Jianmin Bao, Ting Zhang, Dongdong Chen, Weiming Zhang, Lu Yuan, Dong Chen, Fang Wen, Nenghai Yu
The first design is motivated by the observation that using a pretrained MAE to extract the features as the BERT prediction target for masked tokens can achieve better pretraining performance.
Protecting Celebrities from DeepFake with Identity Consistency Transformer
1 code implementation • CVPR 2022 • Xiaoyi Dong, Jianmin Bao, Dongdong Chen, Ting Zhang, Weiming Zhang, Nenghai Yu, Dong Chen, Fang Wen, Baining Guo
In this work we propose Identity Consistency Transformer, a novel face forgery detection method that focuses on high-level semantics, specifically identity information, and detecting a suspect face by finding identity inconsistency in inner and outer face regions.
MBRS : Enhancing Robustness of DNN-based Watermarking by Mini-Batch of Real and Simulated JPEG Compression
1 code implementation • 18 Aug 2021 • Zhaoyang Jia, Han Fang, Weiming Zhang
To address such limitations, we proposed a novel end-to-end training architecture, which utilizes Mini-Batch of Real and Simulated JPEG compression (MBRS) to enhance the JPEG robustness.
Diversity-Aware Meta Visual Prompting
1 code implementation • CVPR 2023 • Qidong Huang, Xiaoyi Dong, Dongdong Chen, Weiming Zhang, Feifei Wang, Gang Hua, Nenghai Yu
We present Diversity-Aware Meta Visual Prompting~(DAM-VP), an efficient and effective prompting method for transferring pre-trained models to downstream tasks with frozen backbone.
Model Watermarking for Image Processing Networks
1 code implementation • 25 Feb 2020 • Jie Zhang, Dong-Dong Chen, Jing Liao, Han Fang, Weiming Zhang, Wenbo Zhou, HAO CUI, Nenghai Yu
In this way, when the attacker trains one surrogate model by using the input-output pairs of the target model, the hidden watermark will be learned and extracted afterward.
Deep Model Intellectual Property Protection via Deep Watermarking
1 code implementation • 8 Mar 2021 • Jie Zhang, Dongdong Chen, Jing Liao, Weiming Zhang, Huamin Feng, Gang Hua, Nenghai Yu
By jointly training the target model and watermark embedding, the extra barrier can even be absorbed into the target model.
CodeApex: A Bilingual Programming Evaluation Benchmark for Large Language Models
1 code implementation • 5 Sep 2023 • Lingyue Fu, Huacan Chai, Shuang Luo, Kounianhua Du, Weiming Zhang, Longteng Fan, Jiayi Lei, Renting Rui, Jianghao Lin, Yuchen Fang, Yifan Liu, Jingkuan Wang, Siyuan Qi, Kangning Zhang, Weinan Zhang, Yong Yu
With the emergence of Large Language Models (LLMs), there has been a significant improvement in the programming capabilities of models, attracting growing attention from researchers.
Shape-invariant 3D Adversarial Point Clouds
1 code implementation • CVPR 2022 • Qidong Huang, Xiaoyi Dong, Dongdong Chen, Hang Zhou, Weiming Zhang, Nenghai Yu
In this paper, we propose a novel Point-Cloud Sensitivity Map to boost both the efficiency and imperceptibility of point perturbations.
GreedyFool: Distortion-Aware Sparse Adversarial Attack
1 code implementation • NeurIPS 2020 • Xiaoyi Dong, Dongdong Chen, Jianmin Bao, Chuan Qin, Lu Yuan, Weiming Zhang, Nenghai Yu, Dong Chen
Sparse adversarial samples are a special branch of adversarial samples that can fool the target model by only perturbing a few pixels.
X-Paste: Revisiting Scalable Copy-Paste for Instance Segmentation using CLIP and StableDiffusion
1 code implementation • 7 Dec 2022 • Hanqing Zhao, Dianmo Sheng, Jianmin Bao, Dongdong Chen, Dong Chen, Fang Wen, Lu Yuan, Ce Liu, Wenbo Zhou, Qi Chu, Weiming Zhang, Nenghai Yu
We demonstrate for the first time that using a text2image model to generate images or zero-shot recognition model to filter noisily crawled images for different object categories is a feasible way to make Copy-Paste truly scalable.
 Ranked #7 on
Instance Segmentation
on LVIS v1.0 val
Ranked #7 on
Instance Segmentation
on LVIS v1.0 val
Watermarking Text Generated by Black-Box Language Models
1 code implementation • 14 May 2023 • Xi Yang, Kejiang Chen, Weiming Zhang, Chang Liu, Yuang Qi, Jie Zhang, Han Fang, Nenghai Yu
To allow third-parties to autonomously inject watermarks into generated text, we develop a watermarking framework for black-box language model usage scenarios.
Pseudo Label-Guided Model Inversion Attack via Conditional Generative Adversarial Network
1 code implementation • 20 Feb 2023 • Xiaojian Yuan, Kejiang Chen, Jie Zhang, Weiming Zhang, Nenghai Yu, Yang Zhang
At first, a top-n selection strategy is proposed to provide pseudo-labels for public data, and use pseudo-labels to guide the training of the cGAN.
Passport-aware Normalization for Deep Model Protection
1 code implementation • NeurIPS 2020 • Jie Zhang, Dongdong Chen, Jing Liao, Weiming Zhang, Gang Hua, Nenghai Yu
Only when the model IP is suspected to be stolen by someone, the private passport-aware branch is added back for ownership verification.
Improving Adversarial Robustness of Masked Autoencoders via Test-time Frequency-domain Prompting
1 code implementation • ICCV 2023 • Qidong Huang, Xiaoyi Dong, Dongdong Chen, Yinpeng Chen, Lu Yuan, Gang Hua, Weiming Zhang, Nenghai Yu
Based on our analysis, we provide a simple yet effective way to boost the adversarial robustness of MAE.
Poison Ink: Robust and Invisible Backdoor Attack
1 code implementation • 5 Aug 2021 • Jie Zhang, Dongdong Chen, Qidong Huang, Jing Liao, Weiming Zhang, Huamin Feng, Gang Hua, Nenghai Yu
As the image structure can keep its semantic meaning during the data transformation, such trigger pattern is inherently robust to data transformations.
DUP-Net: Denoiser and Upsampler Network for 3D Adversarial Point Clouds Defense
1 code implementation • ICCV 2019 • Hang Zhou, Kejiang Chen, Weiming Zhang, Han Fang, Wenbo Zhou, Nenghai Yu
We propose a Denoiser and UPsampler Network (DUP-Net) structure as defenses for 3D adversarial point cloud classification, where the two modules reconstruct surface smoothness by dropping or adding points.
Gaussian Shading: Provable Performance-Lossless Image Watermarking for Diffusion Models
1 code implementation • 7 Apr 2024 • Zijin Yang, Kai Zeng, Kejiang Chen, Han Fang, Weiming Zhang, Nenghai Yu
To address this issue, we propose Gaussian Shading, a diffusion model watermarking technique that is both performance-lossless and training-free, while serving the dual purpose of copyright protection and tracing of offending content.
Control Risk for Potential Misuse of Artificial Intelligence in Science
1 code implementation • 11 Dec 2023 • Jiyan He, Weitao Feng, Yaosen Min, Jingwei Yi, Kunsheng Tang, Shuai Li, Jie Zhang, Kejiang Chen, Wenbo Zhou, Xing Xie, Weiming Zhang, Nenghai Yu, Shuxin Zheng
In this study, we aim to raise awareness of the dangers of AI misuse in science, and call for responsible AI development and use in this domain.
Adversarial Examples Detection beyond Image Space
1 code implementation • 23 Feb 2021 • Kejiang Chen, Yuefeng Chen, Hang Zhou, Chuan Qin, Xiaofeng Mao, Weiming Zhang, Nenghai Yu
To detect both few-perturbation attacks and large-perturbation attacks, we propose a method beyond image space by a two-stream architecture, in which the image stream focuses on the pixel artifacts and the gradient stream copes with the confidence artifacts.
Data-Free Hard-Label Robustness Stealing Attack
1 code implementation • 10 Dec 2023 • Xiaojian Yuan, Kejiang Chen, Wen Huang, Jie Zhang, Weiming Zhang, Nenghai Yu
In response to these identified gaps, we introduce a novel Data-Free Hard-Label Robustness Stealing (DFHL-RS) attack in this paper, which enables the stealing of both model accuracy and robustness by simply querying hard labels of the target model without the help of any natural data.
Self-supervised Adversarial Training
1 code implementation • 15 Nov 2019 • Kejiang Chen, Hang Zhou, Yuefeng Chen, Xiaofeng Mao, Yuhong Li, Yuan He, Hui Xue, Weiming Zhang, Nenghai Yu
Recent work has demonstrated that neural networks are vulnerable to adversarial examples.
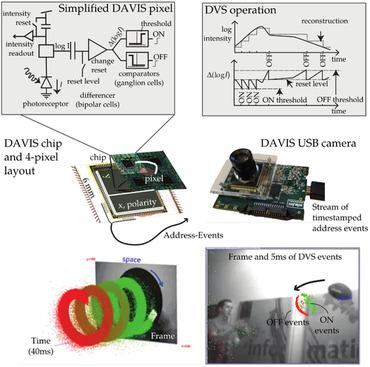
Deep Learning for Event-based Vision: A Comprehensive Survey and Benchmarks
1 code implementation • 17 Feb 2023 • Xu Zheng, Yexin Liu, Yunfan Lu, Tongyan Hua, Tianbo Pan, Weiming Zhang, DaCheng Tao, Lin Wang
Event cameras are bio-inspired sensors that capture the per-pixel intensity changes asynchronously and produce event streams encoding the time, pixel position, and polarity (sign) of the intensity changes.
Worst-Case-Aware Curriculum Learning for Zero and Few Shot Transfer
1 code implementation • 23 Sep 2020 • Sheng Zhang, Xin Zhang, Weiming Zhang, Anders Søgaard
Multi-task transfer learning based on pre-trained language encoders achieves state-of-the-art performance across a range of tasks.
Enhanced Attacks on Defensively Distilled Deep Neural Networks
no code implementations • 16 Nov 2017 • Yujia Liu, Weiming Zhang, Shaohua Li, Nenghai Yu
In this paper, we first propose the epsilon-neighborhood attack, which can fool the defensively distilled networks with 100% success rate in the white-box setting, and it is fast to generate adversarial examples with good visual quality.
Detection based Defense against Adversarial Examples from the Steganalysis Point of View
no code implementations • CVPR 2019 • Jiayang Liu, Weiming Zhang, Yiwei Zhang, Dongdong Hou, Yujia Liu, Hongyue Zha, Nenghai Yu
Moreover, secondary adversarial attacks cannot be directly performed to our method because our method is not based on a neural network but based on high-dimensional artificial features and FLD (Fisher Linear Discriminant) ensemble.
Unauthorized AI cannot Recognize Me: Reversible Adversarial Example
no code implementations • 1 Nov 2018 • Jiayang Liu, Weiming Zhang, Kazuto Fukuchi, Youhei Akimoto, Jun Sakuma
In this study, we propose a new methodology to control how user's data is recognized and used by AI via exploiting the properties of adversarial examples.
CAAD 2018: Powerful None-Access Black-Box Attack Based on Adversarial Transformation Network
no code implementations • 3 Nov 2018 • Xiaoyi Dong, Weiming Zhang, Nenghai Yu
In this paper, we propose an improvement of Adversarial Transformation Networks(ATN) to generate adversarial examples, which can fool white-box models and black-box models with a state of the art performance and won the 2rd place in the non-target task in CAAD 2018.
Emerging Applications of Reversible Data Hiding
no code implementations • 7 Nov 2018 • Dongdong Hou, Weiming Zhang, Jiayang Liu, Siyan Zhou, Dong-Dong Chen, Nenghai Yu
Reversible data hiding (RDH) is one special type of information hiding, by which the host sequence as well as the embedded data can be both restored from the marked sequence without loss.
CAAD 2018: Iterative Ensemble Adversarial Attack
no code implementations • 7 Nov 2018 • Jiayang Liu, Weiming Zhang, Nenghai Yu
Deep Neural Networks (DNNs) have recently led to significant improvements in many fields.
Neural Machine Reading Comprehension: Methods and Trends
no code implementations • 2 Jul 2019 • Shanshan Liu, Xin Zhang, Sheng Zhang, Hui Wang, Weiming Zhang
Machine reading comprehension (MRC), which requires a machine to answer questions based on a given context, has attracted increasing attention with the incorporation of various deep-learning techniques over the past few years.
Once a MAN: Towards Multi-Target Attack via Learning Multi-Target Adversarial Network Once
no code implementations • ICCV 2019 • Jiangfan Han, Xiaoyi Dong, Ruimao Zhang, Dong-Dong Chen, Weiming Zhang, Nenghai Yu, Ping Luo, Xiaogang Wang
Recently, generation-based methods have received much attention since they directly use feed-forward networks to generate the adversarial samples, which avoid the time-consuming iterative attacking procedure in optimization-based and gradient-based methods.
Reversible Adversarial Attack based on Reversible Image Transformation
no code implementations • 6 Nov 2019 • Zhaoxia Yin, Hua Wang, Li Chen, Jie Wang, Weiming Zhang
In order to prevent illegal or unauthorized access of image data such as human faces and ensure legitimate users can use authorization-protected data, reversible adversarial attack technique is rise.
LG-GAN: Label Guided Adversarial Network for Flexible Targeted Attack of Point Cloud-based Deep Networks
no code implementations • 1 Nov 2020 • Hang Zhou, Dongdong Chen, Jing Liao, Weiming Zhang, Kejiang Chen, Xiaoyi Dong, Kunlin Liu, Gang Hua, Nenghai Yu
To overcome these shortcomings, this paper proposes a novel label guided adversarial network (LG-GAN) for real-time flexible targeted point cloud attack.
Identity-Driven DeepFake Detection
no code implementations • 7 Dec 2020 • Xiaoyi Dong, Jianmin Bao, Dongdong Chen, Weiming Zhang, Nenghai Yu, Dong Chen, Fang Wen, Baining Guo
Our approach takes as input the suspect image/video as well as the target identity information (a reference image or video).
Improved Image Matting via Real-time User Clicks and Uncertainty Estimation
no code implementations • CVPR 2021 • Tianyi Wei, Dongdong Chen, Wenbo Zhou, Jing Liao, Hanqing Zhao, Weiming Zhang, Nenghai Yu
Image matting is a fundamental and challenging problem in computer vision and graphics.
Spatial-Phase Shallow Learning: Rethinking Face Forgery Detection in Frequency Domain
no code implementations • CVPR 2021 • Honggu Liu, Xiaodan Li, Wenbo Zhou, Yuefeng Chen, Yuan He, Hui Xue, Weiming Zhang, Nenghai Yu
The remarkable success in face forgery techniques has received considerable attention in computer vision due to security concerns.
A Brief Survey on Deep Learning Based Data Hiding
no code implementations • 2 Mar 2021 • Chaoning Zhang, Chenguo Lin, Philipp Benz, Kejiang Chen, Weiming Zhang, In So Kweon
Data hiding is the art of concealing messages with limited perceptual changes.
A Local Similarity-Preserving Framework for Nonlinear Dimensionality Reduction with Neural Networks
no code implementations • 10 Mar 2021 • Xiang Wang, Xiaoyong Li, Junxing Zhu, Zichen Xu, Kaijun Ren, Weiming Zhang, Xinwang Liu, Kui Yu
Real-world data usually have high dimensionality and it is important to mitigate the curse of dimensionality.
Reversible Watermarking in Deep Convolutional Neural Networks for Integrity Authentication
no code implementations • 9 Apr 2021 • Xiquan Guan, Huamin Feng, Weiming Zhang, Hang Zhou, Jie Zhang, Nenghai Yu
Specifically, we present the reversible watermarking problem of deep convolutional neural networks and utilize the pruning theory of model compression technology to construct a host sequence used for embedding watermarking information by histogram shift.
Exploring Structure Consistency for Deep Model Watermarking
no code implementations • 5 Aug 2021 • Jie Zhang, Dongdong Chen, Jing Liao, Han Fang, Zehua Ma, Weiming Zhang, Gang Hua, Nenghai Yu
However, little attention has been devoted to the protection of DNNs in image processing tasks.
Speech Pattern based Black-box Model Watermarking for Automatic Speech Recognition
no code implementations • 19 Oct 2021 • Haozhe Chen, Weiming Zhang, Kunlin Liu, Kejiang Chen, Han Fang, Nenghai Yu
As an effective method for intellectual property (IP) protection, model watermarking technology has been applied on a wide variety of deep neural networks (DNN), including speech classification models.
 Automatic Speech Recognition
Automatic Speech Recognition
 Automatic Speech Recognition (ASR)
+2
Automatic Speech Recognition (ASR)
+2
Sociolectal Analysis of Pretrained Language Models
no code implementations • EMNLP 2021 • Sheng Zhang, Xin Zhang, Weiming Zhang, Anders Søgaard
Using data from English cloze tests, in which subjects also self-reported their gender, age, education, and race, we examine performance differences of pretrained language models across demographic groups, defined by these (protected) attributes.
Tracing Text Provenance via Context-Aware Lexical Substitution
no code implementations • 15 Dec 2021 • Xi Yang, Jie Zhang, Kejiang Chen, Weiming Zhang, Zehua Ma, Feng Wang, Nenghai Yu
Tracing text provenance can help claim the ownership of text content or identify the malicious users who distribute misleading content like machine-generated fake news.
Self-supervised Transformer for Deepfake Detection
no code implementations • 2 Mar 2022 • Hanqing Zhao, Wenbo Zhou, Dongdong Chen, Weiming Zhang, Nenghai Yu
After pre-training with our method, the model will then be partially fine-tuned for deepfake detection task.
Invertible Mask Network for Face Privacy-Preserving
no code implementations • 19 Apr 2022 • Yang Yang, Yiyang Huang, Ming Shi, Kejiang Chen, Weiming Zhang, Nenghai Yu
Then, put the "Mask" face onto the protected face and generate the masked face, in which the masked face is indistinguishable from "Mask" face.
MaskCLIP: Masked Self-Distillation Advances Contrastive Language-Image Pretraining
no code implementations • CVPR 2023 • Xiaoyi Dong, Jianmin Bao, Yinglin Zheng, Ting Zhang, Dongdong Chen, Hao Yang, Ming Zeng, Weiming Zhang, Lu Yuan, Dong Chen, Fang Wen, Nenghai Yu
Second, masked self-distillation is also consistent with vision-language contrastive from the perspective of training objective as both utilize the visual encoder for feature aligning, and thus is able to learn local semantics getting indirect supervision from the language.
PointCAT: Contrastive Adversarial Training for Robust Point Cloud Recognition
no code implementations • 16 Sep 2022 • Qidong Huang, Xiaoyi Dong, Dongdong Chen, Hang Zhou, Weiming Zhang, Kui Zhang, Gang Hua, Nenghai Yu
Notwithstanding the prominent performance achieved in various applications, point cloud recognition models have often suffered from natural corruptions and adversarial perturbations.
Ada3Diff: Defending against 3D Adversarial Point Clouds via Adaptive Diffusion
no code implementations • 29 Nov 2022 • Kui Zhang, Hang Zhou, Jie Zhang, Qidong Huang, Weiming Zhang, Nenghai Yu
Deep 3D point cloud models are sensitive to adversarial attacks, which poses threats to safety-critical applications such as autonomous driving.
VQNet 2.0: A New Generation Machine Learning Framework that Unifies Classical and Quantum
no code implementations • 9 Jan 2023 • Huanyu Bian, Zhilong Jia, Menghan Dou, Yuan Fang, Lei LI, Yiming Zhao, Hanchao Wang, Zhaohui Zhou, Wei Wang, Wenyu Zhu, Ye Li, Yang Yang, Weiming Zhang, Nenghai Yu, Zhaoyun Chen, Guoping Guo
Therefore, based on VQNet 1. 0, we further propose VQNet 2. 0, a new generation of unified classical and quantum machine learning framework that supports hybrid optimization.
LLM Paternity Test: Generated Text Detection with LLM Genetic Inheritance
no code implementations • 21 May 2023 • Xiao Yu, Yuang Qi, Kejiang Chen, Guoqiang Chen, Xi Yang, Pengyuan Zhu, Weiming Zhang, Nenghai Yu
Large language models (LLMs) can generate texts that carry the risk of various misuses, including plagiarism, planting fake reviews on e-commerce platforms, or creating inflammatory false tweets.
Test-Time Adaptation for Nighttime Color-Thermal Semantic Segmentation
no code implementations • 10 Jul 2023 • Yexin Liu, Weiming Zhang, Guoyang Zhao, Jinjing Zhu, Athanasios Vasilakos, Lin Wang
we propose the first test-time adaptation (TTA) framework, dubbed Night-TTA, to address the problems for nighttime RGBT semantic segmentation without access to the source (daytime) data during adaptation.
Segue: Side-information Guided Generative Unlearnable Examples for Facial Privacy Protection in Real World
no code implementations • 24 Oct 2023 • Zhiling Zhang, Jie Zhang, Kui Zhang, Wenbo Zhou, Weiming Zhang, Nenghai Yu
To address these concerns, researchers are actively exploring the concept of ``unlearnable examples", by adding imperceptible perturbation to data in the model training stage, which aims to prevent the model from learning discriminate features of the target face.
Improving Adversarial Transferability by Stable Diffusion
no code implementations • 18 Nov 2023 • Jiayang Liu, Siyu Zhu, Siyuan Liang, Jie Zhang, Han Fang, Weiming Zhang, Ee-Chien Chang
Various techniques have emerged to enhance the transferability of adversarial attacks for the black-box scenario.
Adapting Large Language Models for Education: Foundational Capabilities, Potentials, and Challenges
no code implementations • 27 Dec 2023 • Qingyao Li, Lingyue Fu, Weiming Zhang, Xianyu Chen, Jingwei Yu, Wei Xia, Weinan Zhang, Ruiming Tang, Yong Yu
Online education platforms, leveraging the internet to distribute education resources, seek to provide convenient education but often fall short in real-time communication with students.
Model X-ray:Detect Backdoored Models via Decision Boundary
no code implementations • 27 Feb 2024 • Yanghao Su, Jie Zhang, Ting Xu, Tianwei Zhang, Weiming Zhang, Nenghai Yu
To address it, in this paper, we begin by presenting an intriguing observation: the decision boundary of the backdoored model exhibits a greater degree of closeness than that of the clean model.
Towards Generalist Prompting for Large Language Models by Mental Models
no code implementations • 28 Feb 2024 • Haoxiang Guan, Jiyan He, Shuxin Zheng, En-Hong Chen, Weiming Zhang, Nenghai Yu
MeMo distills the cores of various prompting methods into individual mental models and allows LLMs to autonomously select the most suitable mental models for the problem, achieving or being near to the state-of-the-art results on diverse tasks such as STEM, logical reasoning, and commonsense reasoning in zero-shot settings.
GoodSAM: Bridging Domain and Capacity Gaps via Segment Anything Model for Distortion-aware Panoramic Semantic Segmentation
no code implementations • 25 Mar 2024 • Weiming Zhang, Yexin Liu, Xu Zheng, Lin Wang
To this end, we propose a novel framework, called GoodSAM, that introduces a teacher assistant (TA) to provide semantic information, integrated with SAM to generate ensemble logits to achieve knowledge transfer.
Provably Secure Disambiguating Neural Linguistic Steganography
1 code implementation • 26 Mar 2024 • Yuang Qi, Kejiang Chen, Kai Zeng, Weiming Zhang, Nenghai Yu
SyncPool does not change the size of the candidate pool or the distribution of tokens and thus is applicable to provably secure language steganography methods.
Unsupervised Visible-Infrared ReID via Pseudo-label Correction and Modality-level Alignment
no code implementations • 10 Apr 2024 • Yexin Liu, Weiming Zhang, Athanasios V. Vasilakos, Lin Wang
Specifically, to address the first challenge, we propose a pseudo-label correction strategy that utilizes a Beta Mixture Model to predict the probability of mis-clustering based network's memory effect and rectifies the correspondence by adding a perceptual term to contrastive learning.
©Plug-in Authorization for Human Content Copyright Protection in Text-to-Image Model
no code implementations • 18 Apr 2024 • Chao Zhou, Huishuai Zhang, Jiang Bian, Weiming Zhang, Nenghai Yu
To mitigate this, we propose the \copyright Plug-in Authorization framework, introducing three operations: addition, extraction, and combination.